-

-
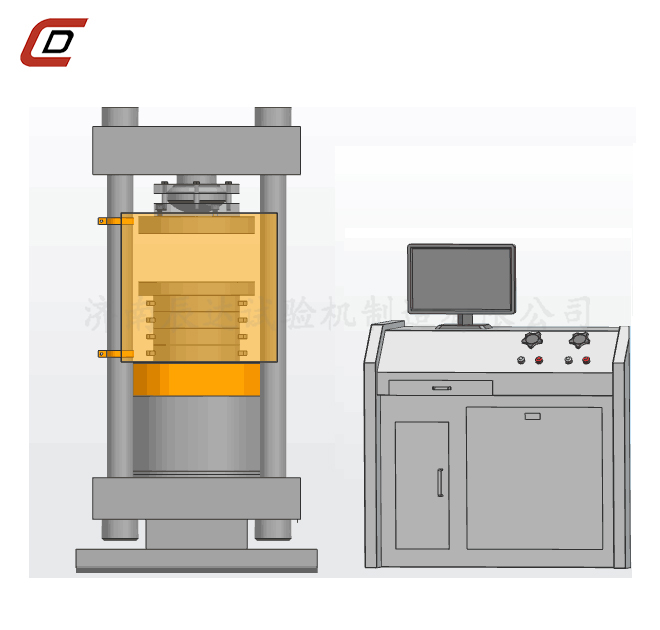
30噸液壓萬能試驗機
產品簡介:
產品概述: 30噸液壓萬能試驗機主機采用油缸下置式主機結構,主要用于金屬材料、非金屬材料、產品零件、部件、結構件,標準件的拉伸、壓縮、彎曲等力學性能試驗。 30噸液壓萬能試驗機若增配環境裝置還可做該環境下的材...
-

-
電子式萬能材料試驗機
產品簡介:
一、產品使用領域: 電子式萬能材料試驗機廣泛用于金屬、非金屬材料的拉、壓、等力學性能試驗,并配以相應的拉伸壓縮附具。適用于質量監督、教學科研、航空航天、鋼鐵冶金、汽車、橡膠塑料、編織材料等各種試驗領域的...
-

-
潤滑油抗磨試驗機
產品簡介:
一. 產品簡介潤滑油抗磨試驗機主要用來做各種潤滑油和脂在滑動摩擦磨損狀態下的承載能力和摩擦磨損特性的試驗;也可以用來做各種金屬材料和非金屬材料(尼龍、塑料等)在滑動摩擦狀態下的耐磨性能的試驗;同時也可以...
-

-
水泥恒應力壓力試驗機
產品簡介:
一、主要功能: 水泥恒應力壓力試驗機是由微機控制、恒速加載自動完成試驗過程,平穩、水平落地即可使用。主要用于巖石、混凝土、水泥制品、空心磚、粉煤灰磚、耐火材料、工程材料、石料、橡膠支座等建筑材料的抗壓強...
-

-
金屬沖擊試驗機
產品簡介:
主要用途:JBW-300B 金屬沖擊試驗機是用于測量金屬材料在動負荷下抵抗沖擊性能的理想的檢測儀器。滿足標準GB/T3808-2002《擺錘式沖擊試驗機的檢驗》,和GB/T229-2007《金屬夏比缺口沖擊試驗方法》,JJG 145-2007 《擺錘式沖擊試驗機...
-

-
金屬線材扭轉試驗機EZ-15、20、30
產品簡介:
金屬線材扭轉試驗機EZ-15、20、30 產品名稱:EZ-15、20、30金屬線材扭轉試驗機 產品型號:EZ-15 EZ-20 EZ-30 產品量程:>10.0mm 產品描述:適用于金屬/非金屬線材在單向或雙向扭轉中承受塑性變形的能力及顯示線材表面和內部的缺陷 一...